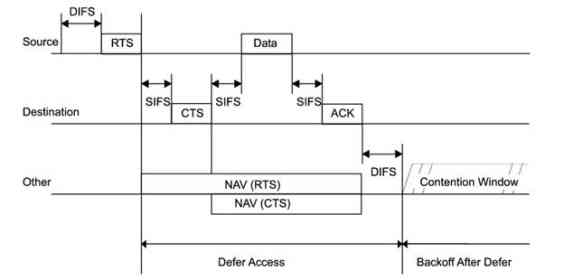
Many people, who know how “WiFi contention mechanism” works, ask that it is really viable to have two same-band radios in the same AP box.
So, you can run one 2.4Ghz and one 5Ghz radio in a single AP box but can you run two 5Ghz radios at the same time.
Here, “at the same” does not mean simultaneous Tx or Rx. One should Tx while the other is receiving. So, basically, they should “interfere” with each other because the Tx and Rx are so close, right? Even if they choose UNI-1 and UNI-2 Ext bands and try to move away from each other in the spectrum view, they should see the interference due to close proximity.
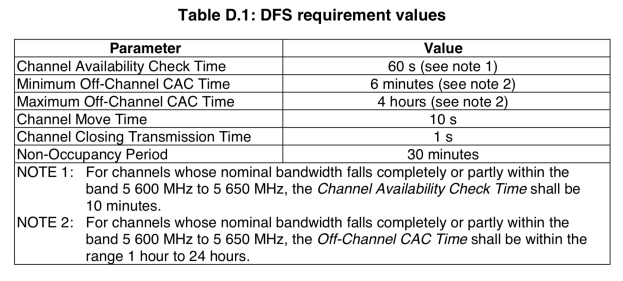
Theoretically, this can be solved via a physical – hardware based filter (band pass filter).
When there is a filter for a radio, that radio only hears what filter “filters” :) The rest is dropped.
So, let’s test if Aruba AP345 dual 5Ghz mode works as expected:
Here we have two SSIDs:
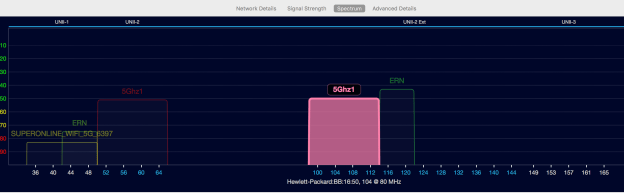
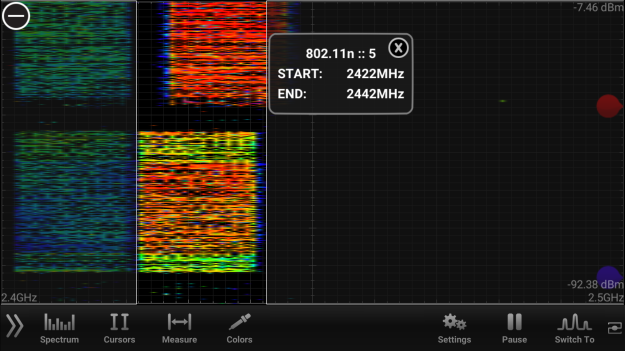
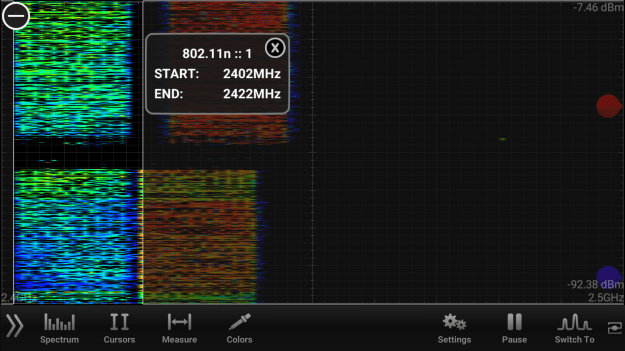
First SSID is 5Ghz1 and it is being broadcast on ch60E (80Mhz wide and it is on UNI2) and the other SSID is again named as 5Ghz1 but on ch104E (80Mhz and UNI2-Ext).
They are being broadcast via a single Aruba AP345. So, both radios on the AP are on 5Ghz, meaning no 2.4Ghz SSID on that AP.
Test Case 1 – Client1 Tx, Client2 Rx (iperf between clients) when they’re connected to the SAME 5Ghz radio.
If we connect two 2×2 11ac clients to the same radio, of course they will share the medium, right?
So, here are the results:
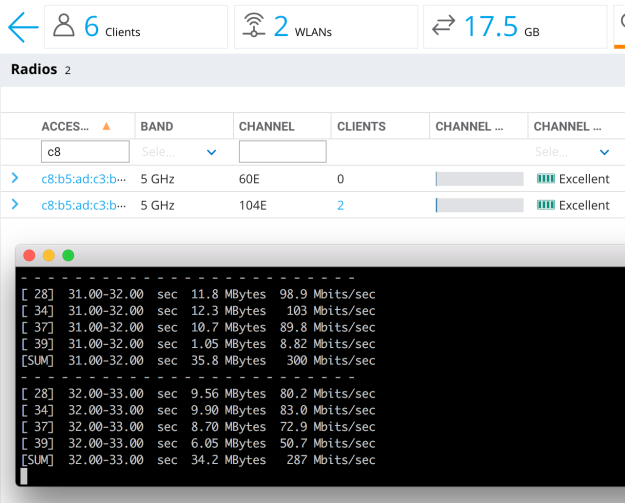
In this case, client one is connected to the 80Mhz SSID with max rate (867Mbps), the other is the same (867Mbps)
..and Client1 is sending traffic to Client2, so basically, they are sharing the air and they are getting around “half” of the total air bandwidth (we can say that 2-stream air bandwidth is around 600Mbps)
So, with air sharing, we’re processing around 300Mbps from each client.
What if we connect one client to radio1-5Ghz and the other client to radio2-5Ghz?
Test Case 2 – Client1 Tx, Client2 Rx (iperf between clients) when they’re connected to the different 5Ghz radios in the same AP.
If those radios are in the same box (very close proximity to each other), they should interfere with each other, so we should be able to get the results similar to test case 1 above, right?
Let’s test this:
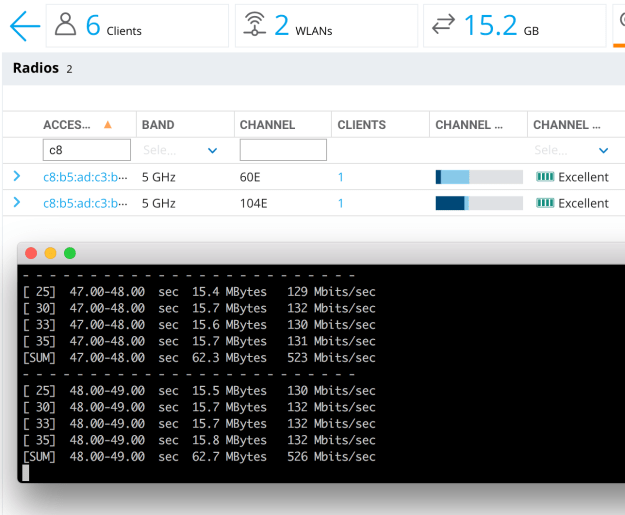
In this test, clients are connected to different radios. Client1 is sending traffic to Client2. So, one radio is shouting at max, while the other is trying to listen.
So, they should interfere and we should see the below adverse effects, right?
1- The performance on the radios should be lower than expected due to excessive noise, so, bad client SNRs. So, low throughput numbers.
2- Transmitting radio is very close the receiving radio, so receiving radio should defer a lot, because of signal (or even energy) detect threshold(s), so receiving radio should suffer a lot.
So, we should see really low throughput numbers due to these effects, so, in the end, that should equal to (or maybe a bit better than) the case number 1 above (connecting to the same radio)
However, in reality, we’re not seeing the adverse effects explained above.
Transmitting radio is sending ~520Mbps data, while the other radio is receiving the same, without affecting each other too much.
So, that means that dual 5Ghz feature on Aruba AP345 just works. That means there is a very strong hardware based filtering between 5Ghz radios and those radios do not interfere with each other even while one radio doing Tx, while the other is doing Rx.
This is very rough test. No RF-cage, no special config tuning or so. I’ve seen that people are talking about Dual-5Ghz, so I grabbed an AP345 and did the test between my computer and my phone. AOS 8.4.0.1.
Summary
Aruba AP345 has the correct level of filtering between 5Ghz radios. When one WiFi client is sending data to another WiFi client (one radio Tx, the other radio Rx scenario), here are the results:
If the clients are connected to the same radio, throughput between clients: ~280Mbps
If the clients are connected to the different 5Ghz radios in the same AP, throughput between clients: ~520Mbps.